RSA SecurID Algorithm Cryptanalysis
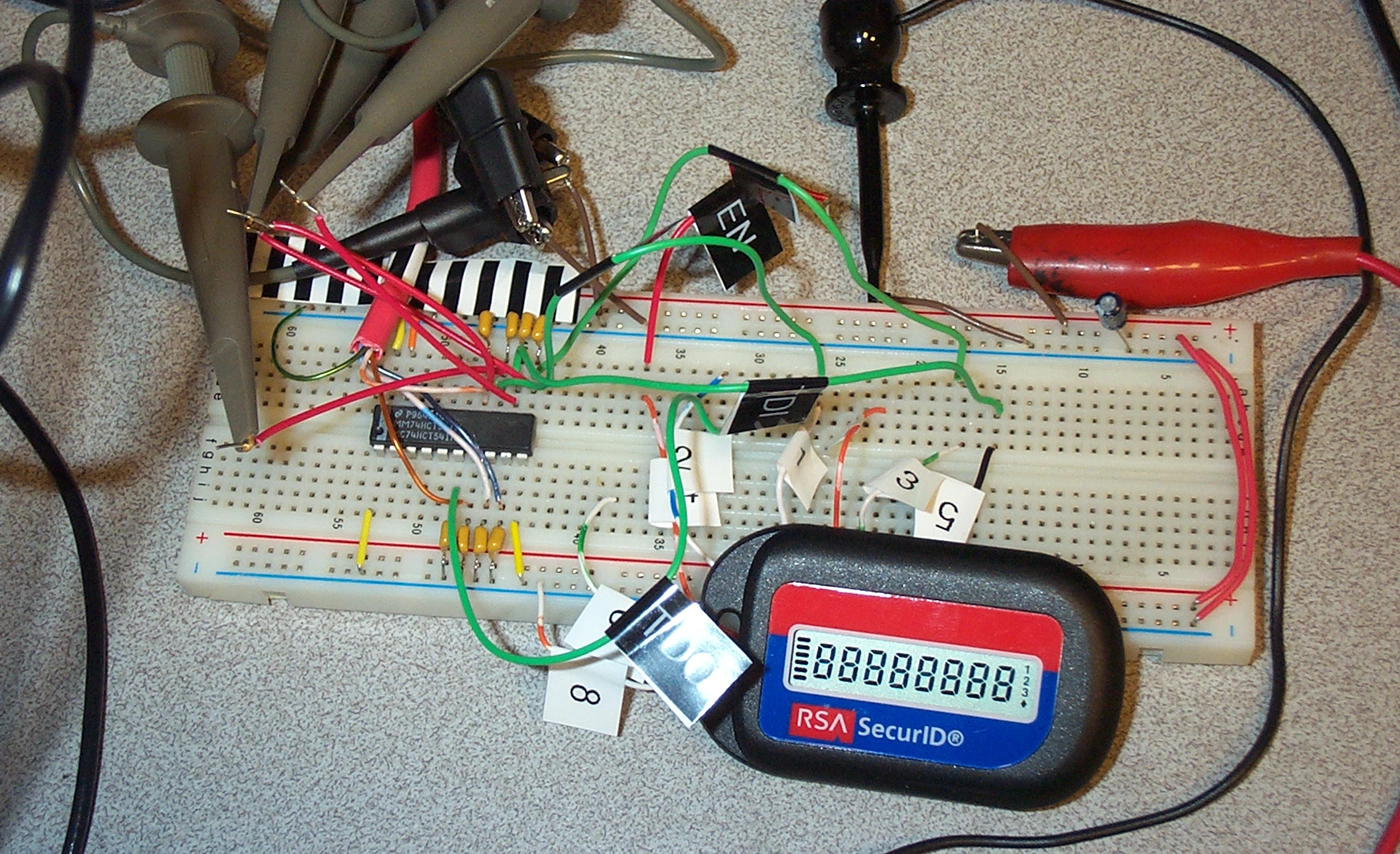
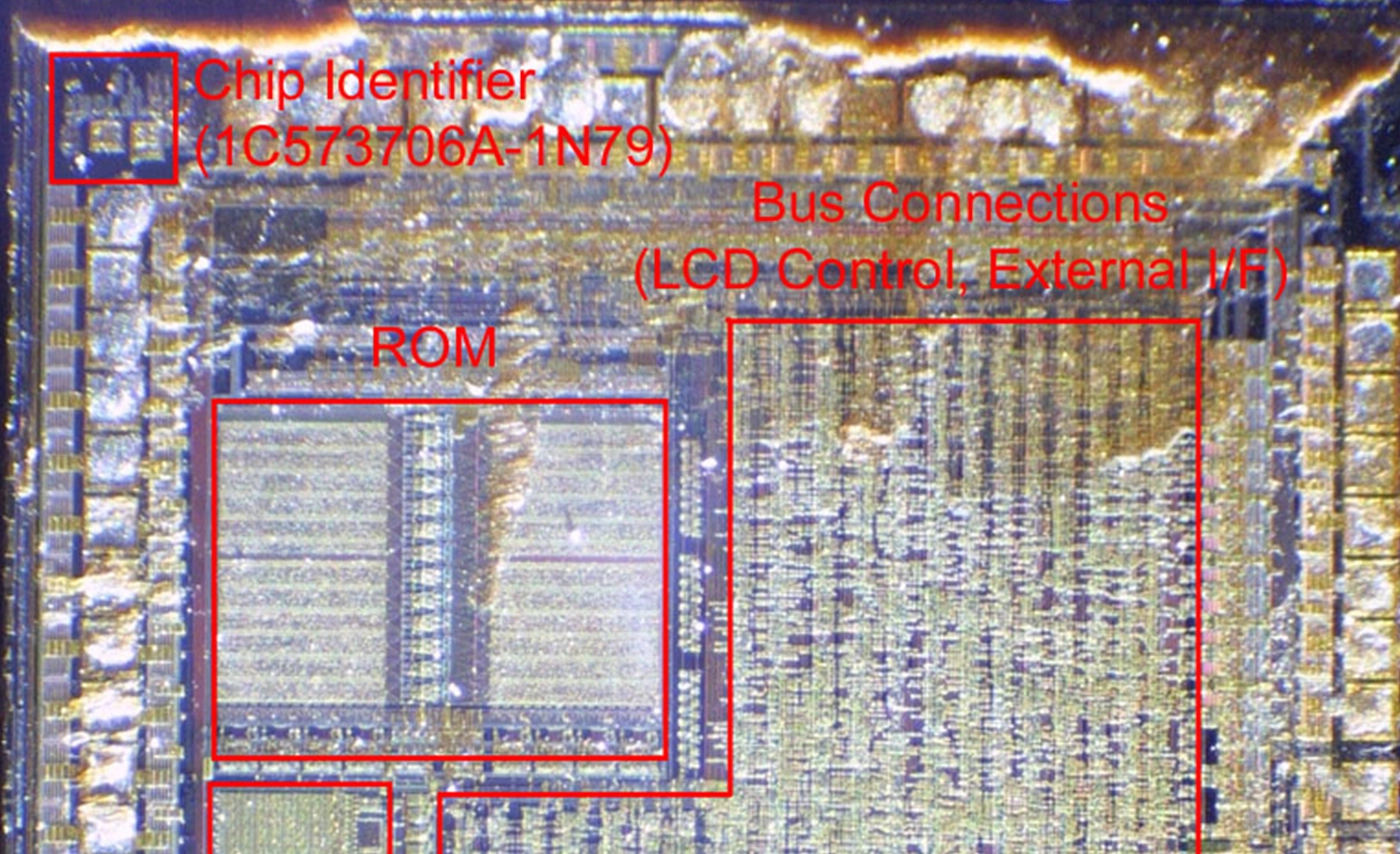
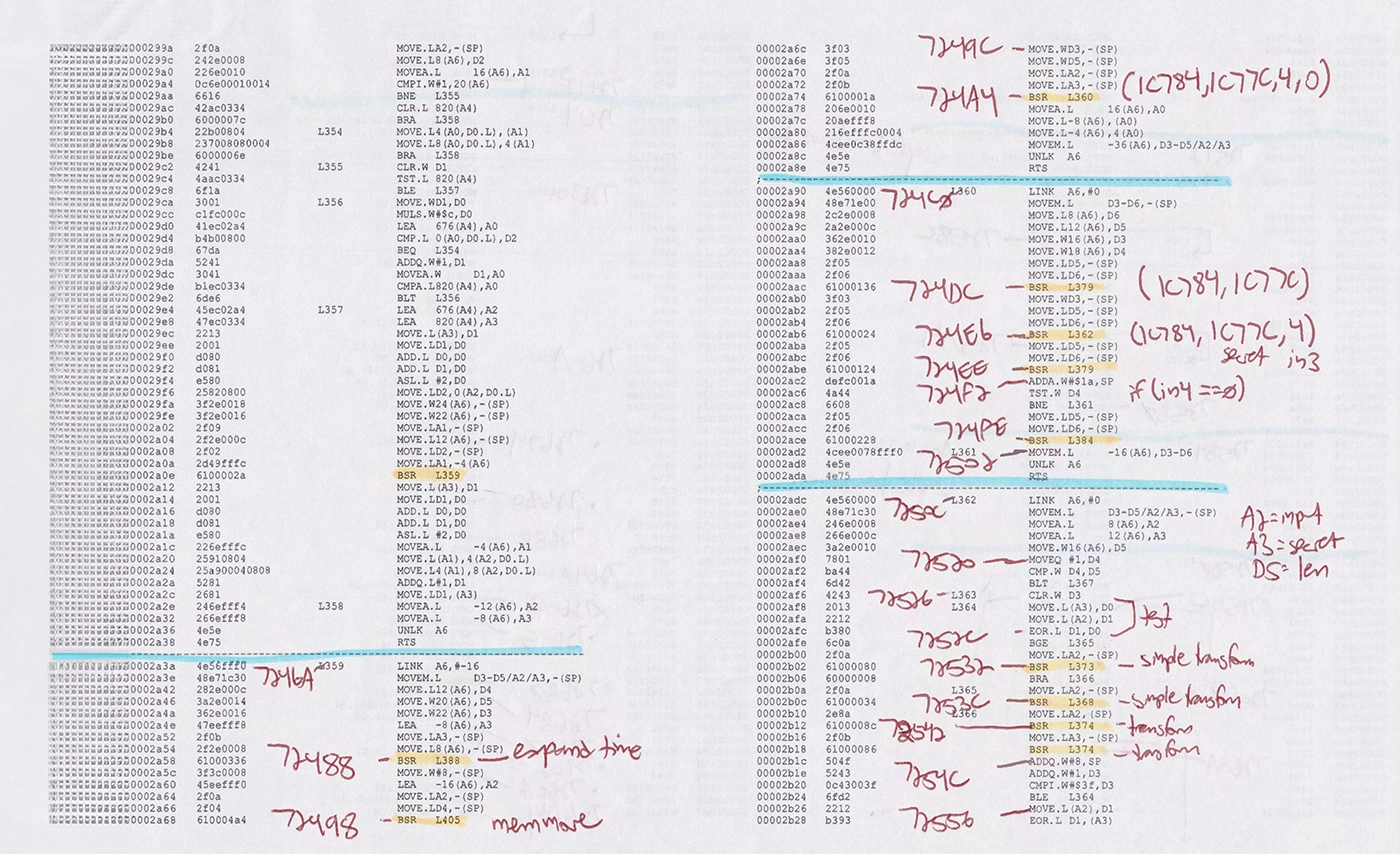
This short paper examines several discovered statistical irregularities in functions used within the RSA Security's SecurID algorithm: the time computation and final conversion routines. Where and how these irregularities can be mitigated by usage and policy are explored. The primary concern is the possibility to generate a complete cycle of tokencode outputs given a known secret, which is equivalent to the cloning of a token device.
Paper: Initial Cryptanalysis of the RSA SecurID Algorithm
Originally released on the @stake website.