PCB Deconstruction Techniques
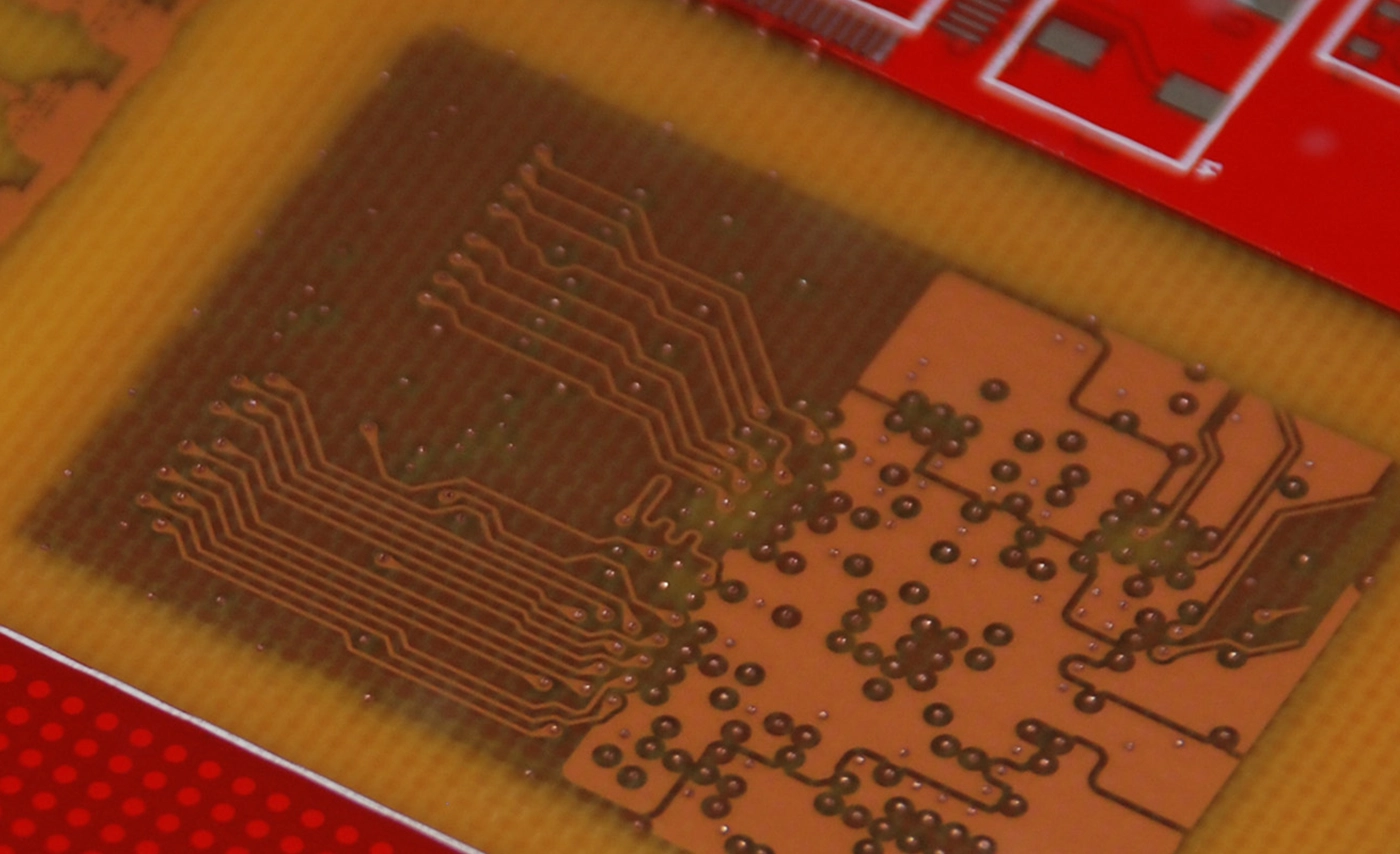
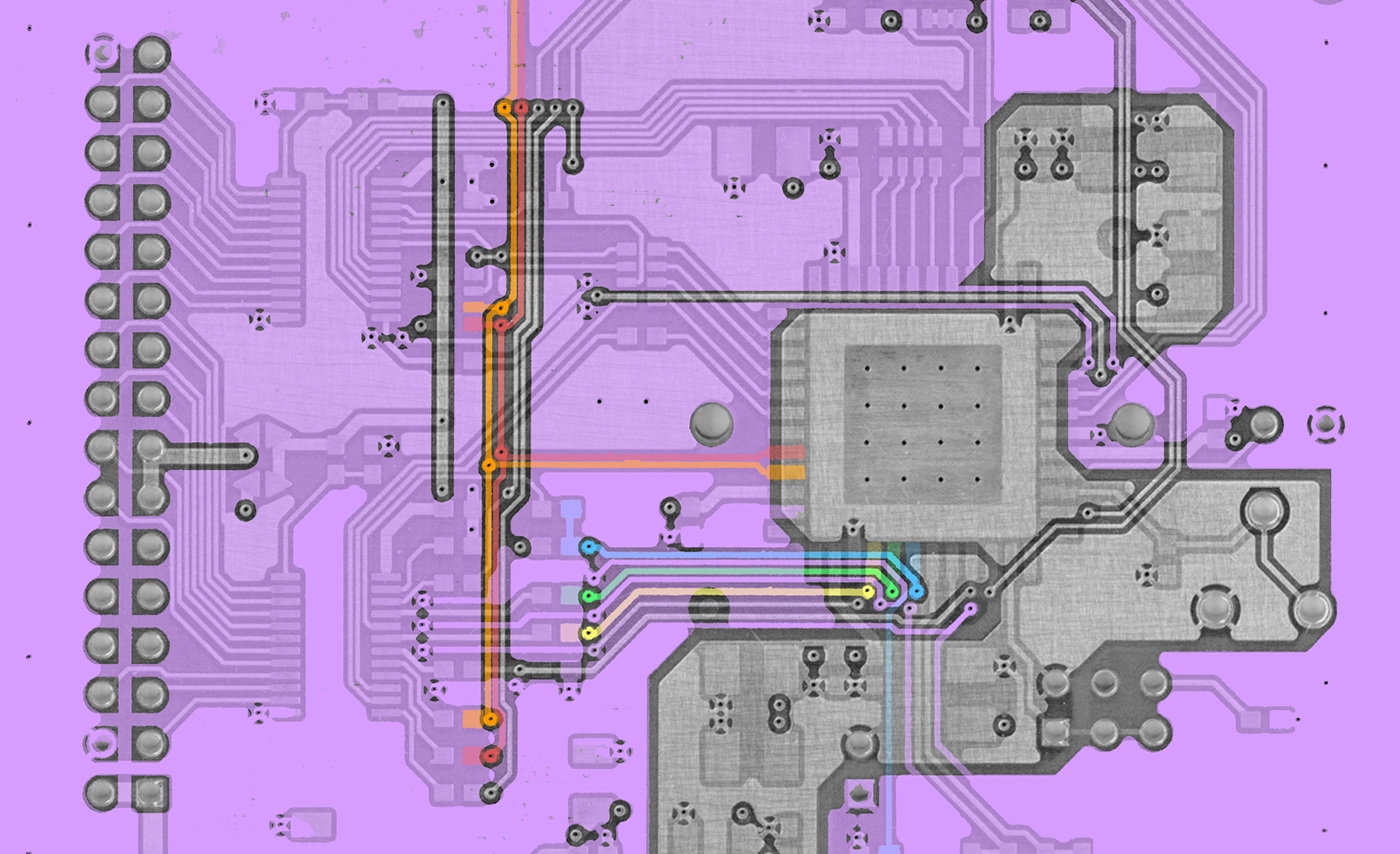
Printed Circuit Boards (PCBs), used within nearly every electronic product in the world, are physical carriers for electronic components and provide conductive pathways between them.
By accessing each individual copper layer of a PCB, one can clone the design, identify areas where new features/capabilities can be inserted, locate specific connections/interfaces, or derive how a product works by creating a schematic diagram.
Presentations:
- Deconstructing the Circuit Board Sandwich: Effective Techniques for PCB Reverse Engineering
Created as a sandwich of alternating copper and insulating substrate layers, PCBs can reveal clues about system functionality based on layout features or how components are interconnected. This presentation details a variety of inexpensive, home-based solutions and state-of-the-art technologies that can facilitate PCB reverse engineering through solder mask removal, delayering, and non-destructive imaging.
Originally presented at DEFCON 22, August 10, 2014.
- Using Superpowers for Hardware Reverse Engineering
Superpowers, normally used by superheroes in the battle of good versus evil, are also accessible to engineers and hackers in equipment used for failure analysis and verification of PCB fabrication and component assembly processes. This presentation examines the use of lasers, X-rays, and sound waves to aid in the reverse engineering of electronic products and circuit boards.
Originally presented at EE Live!, April 3, 2014.
Papers:
- Printed Circuit Board Deconstruction Techniques
The primary purpose of PCB reverse engineering is to determine electronic system or subsystem functionality by analyzing how components are interconnected. We performed a series of experiments using both inexpensive home-based solutions and state-of-the-art technologies with a goal of removing exterior coatings and accessing individual PCB layers. This paper presents our results from the most effective techniques.
Published in the Proceedings of the 8th USENIX Workshop on Offensive Technologies (WOOT '14), San Diego, CA, August 19, 2014.
Additional Resources:
- Video: PCB Deconstruction Techniques Playlist (YouTube)
- Article: Introduction to Delayering and Reversing PCBs (International Journal of PoC||GTFO 0x06)